With the increasing popularity of remote work, the demand for electronic signatures (“eSignatures” or “e-signatures”) has skyrocketed. Employees may be working from home but businesses still need to continue operations and obtain properly signed documents.
They must still sign off on purchases, onboard new hires, and approve invoices. With e-signatures, users can easily sign electronic documents online using their mouse, stylus, or touchscreen device. Businesses can still enforce corporate policies and proper governance.
Electronic signature software also speeds up these everyday activities since there’s no need for printing, signing, scanning, and filing. Managers can even electronically sign off on a PO or new hire using their mobile device at any time and from anywhere.
But are electronic signatures legally binding? In this piece, we’ll tell you everything you need to know about whether your e-signature is legal or not.
Electronic Signature Laws
Electronic signatures are defined in the United States as:
Any electronic sound, symbol, process that is attached to or somehow associated with a record or contract and executed by a party with intention to sign.
That is, electronic signatures include a variety of ways to sign documents electronically without a traditional pen and paper signature.
These signatures have been used over the years to electronically sign all manner of legal documents including mortgage contracts, financial documents, employment agreements, leases, student consent forms, non-disclosure agreements, and more.
So, are electronic signatures legally binding? Assuming they meet certain conditions that we describe below, e-signatures are legally binding and have been in the United States for over 20 years. A landmark federal law, the Electronic Signatures in Global and National Commerce (E-SIGN) Act along with the Uniform Electronic Transactions Act (UETA), have created a legal agreement for the use of electronic signatures and ensure that they’re just as legally binding as their paper counterparts.
Forty-seven states, the District of Columbia, Puerto Rico, and the Virgin Islands have simply adopted UETA. New York, Illinois, and Washington all have similar laws making electronic signatures legal.
Since E-SIGN was passed in June 2000, electronic signatures are widely used in business transactions.
Digital Signatures: Meeting the Legal Standard
Electronic and digital signatures are often used interchangeably but they are different in important ways. “Electronic signatures” is a generic term for a wide-ranging set of methods for signing a document electronically without physical ink.
Digital signatures are an implementation of electronic signatures using certain technical protocols. The most common method, adopted by many digital signature providers such as DocuSign and frevvo, is to use Public Key Infrastructure (PKI) and certificates.
PKI helps secure electronic transactions from tampering, which is one of the factors that makes an e-signature legal.
How Does Public Key Infrastructure Work?
Here are the meanings of terms you need to know when it comes to Public Key Infrastructure and digital signatures:
Hash
A hash is a fixed length string of characters generated using a mathematical algorithm and applying it to arbitrarily data. This string is unique to the data being hashed. Changing any part of the data changes the generated hash. The hash is also a one-way function meaning it cannot be reversed to find the data. Popular examples of hash functions are the Secure Hash Algorithm variants (SHA-1, SHA-2, and SHA-256) and Message Digest 5 (MD5).
Private and Public Keys
A pair of keys generated for an entity – a particular individual, website, or organization. The private key is confidential while the public key is freely shared. It’s not possible to generate the private key by knowing the public key.
Certificate Authority
A certificate authority (CA) is a trusted third party that guarantees the identity of an entity. The CA will generate a private-public key pair or certify that an existing public key is associated with the entity in question. Once validated, the CA will issue a digital certificate that’s signed by the CA.
Digital Certificate
The digital certificate is akin to a passport and identifies the entity that owns the certificate. It usually embeds the public key and may also include other desired information.
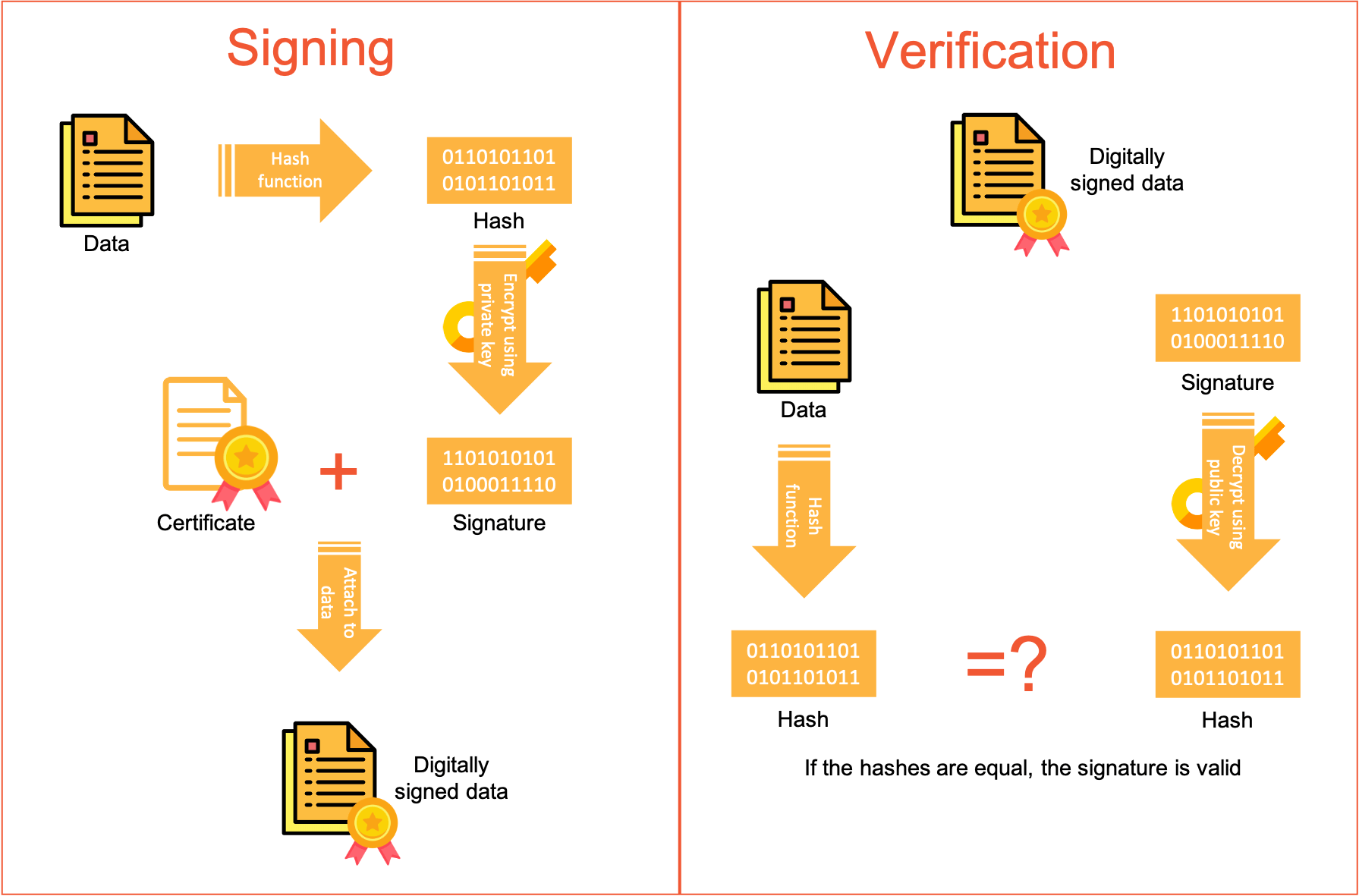
Here’s how a digital signature works in action:
Acme Inc. sends an electronic document over to Jane for digital signature. The steps below unambiguously identify Jane and validate the contents of the document:
- The system first generates a unique hash from the data (contents of the document) and a randomly generated ID. This random ID ensures that the hash is unique every time. So, if Jane signs the same data multiple times, the hash is different each time.
- It then encrypts the hash using Jane’s private key.
- The document along with the encrypted hash and Jane’s digital certificate is sent electronically to Acme.
- Acme generates their own hash from the document contents.
- Acme obtains Jane’s public key from her digital certificate and decrypts the hash that Jane sent.
- They can compare the two hash functions and verify that they are identical. If they are, the digital signature and the document contents are valid.
The difficulty with PKI is that most people don’t actually have private and public keys and the associated digital certificates. Without access to these components, they can’t actually sign electronic documents digitally, rendering the secure infrastructure–and legal effect–moot.
What Makes Electronic Signatures Legally Binding?
E-signature solutions can dramatically speed up and simplify approvals and contracts in your organization but it’s important to take into account some key aspects to ensure that they’ll be legally admissible in a court of law.
1. Intent to Sign
Whether you’re using traditional wet signatures on paper or electronic signatures, a signed contract is only enforceable if there is evidence of the signer’s intent to execute the agreement.
This can be fulfilled by a variety of means. Often the user must check an agreement box, type in their full name and email address, or draw their signature using a touch screen or mouse.
As long as the signatory’s intent to sign can be clearly determined from the record, the e-signature is likely to hold up. Courts have even been known to enforce signed contracts where an email was used as evidence of the signer’s intent to accept the terms of the contract.
2. Reliable Identification of Parties
The identity of any signing party to an electronic transaction must be securely known.
There are many ways to fulfill this requirement. A loose form of verification asks the signer to confirm their email address. More secure systems require signers to first authenticate to the system to confirm the signer’s identity. In situations requiring the utmost security, signers are required to have their own digital certificates so they can be unambiguously linked to the document being signed.
Personal certificates and the underlying infrastructure are cumbersome and expensive to implement and maintain so the vast majority of e-signature applications rely on email or existing login systems.
3. Disclosure and Consent
Parties must be clearly informed of the intended use of a legally binding electronic signature and given the option to agree or to opt out.
In most cases, this requirement is simply fulfilled by providing the appropriate notice or a checkbox that the user must click before signing.
Sometimes, it may be necessary to ensure that the disclosure information is presented in multiple languages, especially for agreements between parties in different countries.
4. Electronic Capture
The system must provide a means to capture an electronic sound, symbol, or process, attached to or logically associated with a transaction or other record and executed or adopted by a person with the intent to sign the record.
In the vast majority of cases, this is achieved simply by asking the user to type in their name and email address or to use a stylus or touchscreen to mimic drawing their signature using a pen.
5. Electronic Transaction Secure From Tampering
Once the electronic transaction has been signed by a party, the relevant data must be secured against tampering and any tampering that might occur must be immediately apparent and detectable.
To meet this requirement, you must use a digital signature with some sort of underlying technical (usually PKI) infrastructure. These signatures employ a “digital hash” of the relevant data that is encrypted using public-private key cryptography. The digital signature can also simultaneously capture and record a signature image and the accurate date and time of capture.
The digital signature can immediately detect any tampering of the digitally signed data or the signature itself. Obviously, the e-signature application must notify users and provide a clear visual indication that the signature is no longer valid.
In frevvo, we’ve designed the system to automatically generate the requisite hash functions for every section that’s digitally signed, encrypt them using the system’s private key, and validate them at every step. It ensures that every digitally signed section is secure from data tampering.
If the frevvo system detects tampering, it displays a red banner indicating invalid data or signature. If the data and signature are valid, the banner is green.
6. Transaction Document Retention
Electronic transaction documents must be retained for somewhat obvious reasons, including later accessibility, compliance with laws and regulations, later enforcement, etc.
For example, you can save documents in the cloud (e.g., Dropbox) or a commercial document management system.
frevvo integrates with Google Drive and other document management systems so you can automatically save any signed documents.
7. Transaction Document Access
The resulting electronic transaction “document” must be available to all parties.
The most common way to handle this requirement is to simply email a copy of the electronically signed document to all parties after the process has been completed. Since the documents are retained, any party can easily obtain a copy of the document at a later date.
In frevvo, you can have the system automatically email all parties and stakeholders–like your HR or accounting department–once a document is executed.
8. Audit Trail for All Transaction Actions
Each action must be recorded in order to be able to prove who did what and when they did it.
This is a key feature that’s not always easy to fulfill. If you’re using email, you’ll need to keep a record of the email trail.
frevvo comes with built-in audit trail functionality, automatically recording who processed each step and when they did it.
Want your e-signatures to be legal and secure?
frevvo makes it easy to create legally-binding online documents with drag-and-drop tools. Try it free for 30 days.
So Which Method of E-Signature Should You Use?
Only frevvo offers the combination of ease of use with completely secure digital signatures that you can be confident meet all the criteria to be legally binding.
| Signature Field, Only | Digital Signature With Email Verification | Digital Signature With Identity Verification | |
|---|---|---|---|
| Intent to sign | ✔︎ | ✔︎ | ✔︎ |
| Reliable identification of parties | ✗ | Probably | ✔︎ |
| Disclosure and consent | ✔︎ | ✔︎ | ✔︎ |
| Electronic capture | ✔︎ | ✔︎ | ✔︎ |
| Electronic transaction secure from tampering | ✗ | ✔︎ | ✔︎ |
| Transaction document retention | ✔︎ | ✔︎ | ✔︎ |
| Transaction document access | ✔︎ | ✔︎ | ✔︎ |
| Audit trail for transaction actions | ✔︎ | ✔︎ | ✔︎ |
| Vendors |  |  |  |
| Legally binding? | Maybe | Probably | Definitely |
Method 1: Signature Field, Only
Use just a signature field only in the least sensitive situations.
Vendors like formstack and Kissflow provide this type of signature with assertions that they’re legally binding.
We’d recommend having an external record like an email thread to ensure that the signature is legitimate.
Since the identity of the parties cannot be reliably determined, nor can the document be secured against tampering, this e-signature is the least secure and therefore least likely to hold up in a court of law.
Method 2: Digital Signature With Email Verification
This digital signature is very similar to DocuSign. The signer gets an email and clicks a link in the email. The document or form is displayed, the signer can enter any required information and apply a signature.
The system will verify identity automatically using the email address and the data is digitally signed using the system’s digital certificate. It’s easy for the person signing since they don’t need to authenticate or supply their own certificate.
The system also automatically detects tampering.
The caveat is that there’s no guaranteed way to determine that the link in the email is being clicked by the person it was sent to. Nevertheless, this is a broadly accepted and widely used digital signature mechanism that’s held up in a court of law numerous times. It’s extremely likely that the e-signature is legally binding.
Method 3: Digital Signature With Identity Verification
This type of signature is the most secure and eliminates the caveats above, which is why it’s the approach we’ve built into frevvo. The document or form can only be accessed by an authenticated person whose identity has been reliably verified.
This electronic signature meets all the requirements for being legally binding without the hassle of requiring individuals to obtain and safeguard their own digital certificates and keys.
It’s easy to use, secure, and legally binding.
How to Capture Legally-Binding Electronic Signatures with frevvo
frevvo provides multiple, flexible options for electronic signatures. Let’s take a look at the ways in which you can set up your workflows so users can sign documents electronically.
Adding a Signature Field
In frevvo’s drag-and-drop form builder, you can drag a signature field from the palette to anywhere onto your form. The end user can simply click anywhere in the signature field and draw their handwritten signature using a trackpad/mouse, stylus, touch screen, or a configured Topaz electronic signature pad.
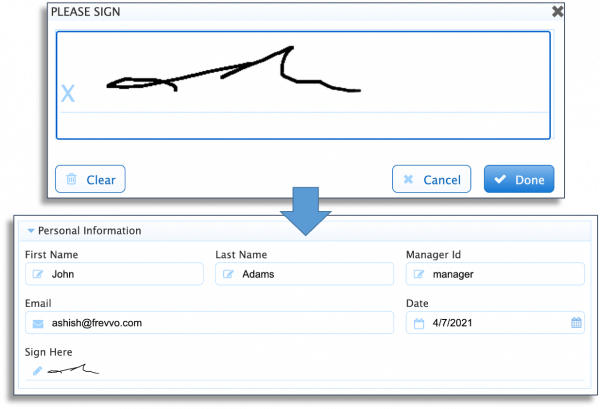
The signature will be displayed on the form.
Securing Digital Signatures
frevvo’s digital signatures verify identity independently of the certificate and private-public keypair that’s used.
You can install in the frevvo cloud server a certificate purchased from a certificate authority or a self-signed certificate. Or you can use frevvo’s own certificate.
It’s much simpler and less cumbersome for users to sign in using their credentials rather than managing their own private-public key infrastructure and digital certificates.
So, frevvo digitally signs sections using a server-side private key and certifies that it has verified the identity of the signer. This provides both reliable identification of signatories while at the same time protecting the data that’s being signed.
Full Identity Verification
This is the most secure type of e-signature.
In frevvo, you can route your document by user or role to ensure that it can only be accessed by an authenticated user with the proper credentials. In order to access the workflow step, the signer must first authenticate (i.e., sign in) to frevvo. This authentication can use frevvo’s built-in login or a single sign-on (SSO) method like Active Directory, SAML, etc.
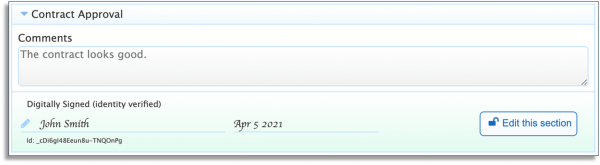
After filling in the fields in the relevant section, the user simply clicks the Sign button for that section. frevvo applies a digital signature since it already knows the identity of the signer, locks the section, and displays a green panel where the signature will be displayed. Fields in the section can no longer be changed.
If the data is tampered with, the signature panel will turn red indicating that the section is no longer valid.
Since signer’s must be authenticated to frevvo, the system automatically verifies the user’s identity and protects the data from unauthorized tampering. It fulfills all the requirements of a legally binding electronic signature.
Email Verification
This is a more secure type of e-signature than the basic signature field but not as secure as full identity verification. It’s commonly used when you need to send documents (like a sales contract) outside of your organization for signature. You don’t want the signer to have to set up an account, remember credentials, etc.
The recipient can click a link in the email to open up the form. After filling in relevant fields, they click the Sign button to sign. In the popup box, they’ll need to type in their first and last name and email address.
frevvo will verify that the email address entered in the box is the same as the address the workflow routed to. Once verified, frevvo will digitally sign the section, lock the data in that section, and display the green panel.
While authentication is not required, the system still verifies the email address automatically and protects the data from unauthorized tampering.
You can try out our document workflows with legally-binding electronic signatures with a 30-day free trial.

